The 5 Levels of Penetration Testing
There is an open secret that few vendors want to discuss: a shocking number of "penetration tests" are nothing more than automated scans with a new cover page. Don't get scammed by these "cheap pentests". This blog post helps you separate out noisy security theater that wastes your time from true security that saves you time and builds trust with your customers.
Imagine paying for a structural engineer to inspect your home's foundation, only to have them walk around the perimeter, glance at the windows, and hand you a bill for thousands of dollars. That is effectively what happens when you purchase a "cheap" pentest.
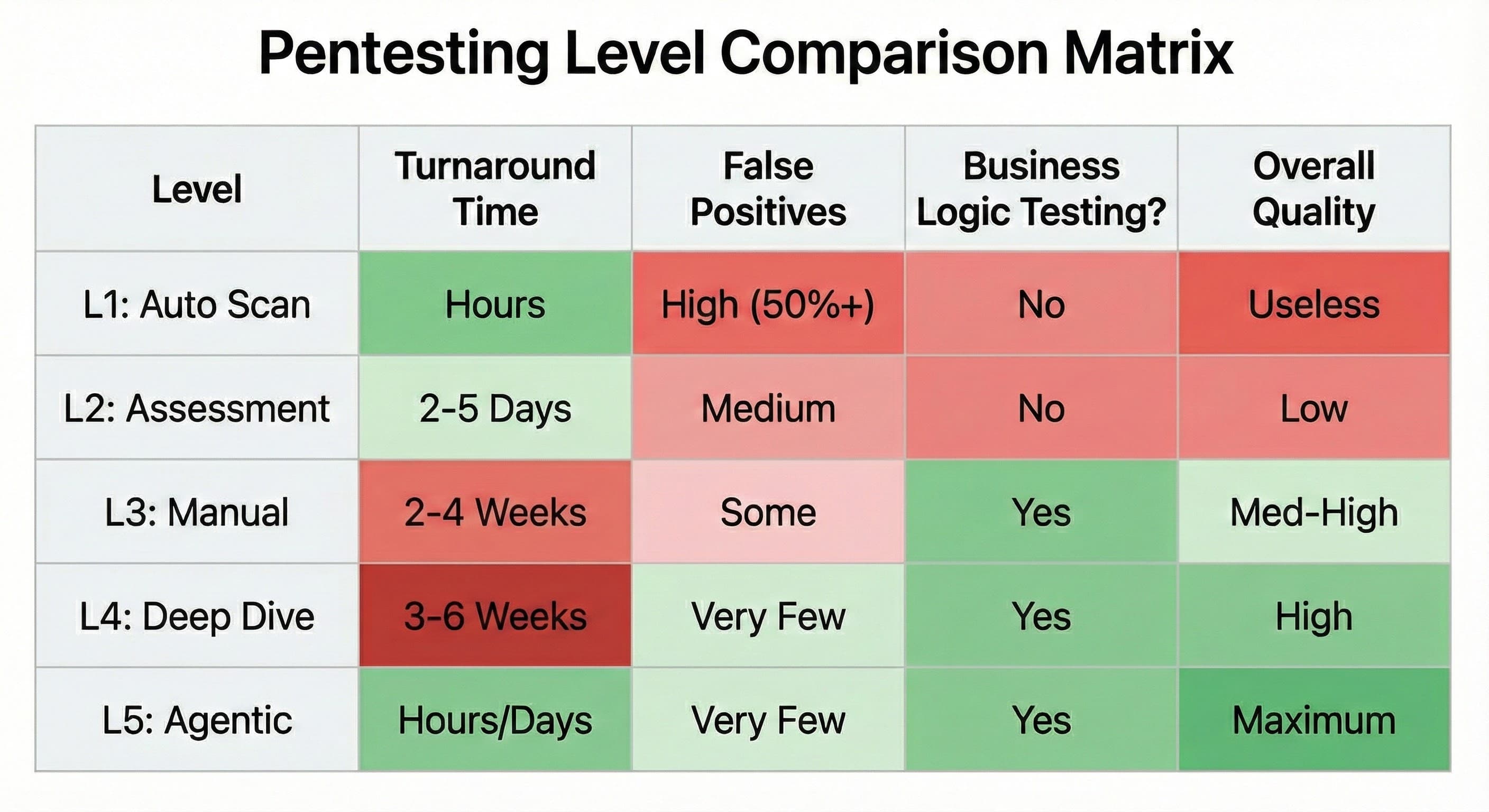
If you are paying for security assurance, you deserve to know exactly what level of testing you are receiving. Before signing your next vendor contract, you should know the difference between these five distinct levels of security testing. Learn how to spot the difference between a basic automated sweep and a real attack simulation.
Level 1: Automated Vulnerability Scan (The "Automated Sweep")
This is the baseline of security testing. It involves pointing an automated tool (like Nessus, Qualys, or a BurpSuite scan) at your application and hitting "Go." The scam happens when a vendor sells this to you as a "penetration test." It is not. Frankly, it is often useless.
- Turnaround Time: Immediate to Hours.
- False Positives: High (50%+).
- Quality: Useless.
Simple scanners lack context and drown your team in noise. If a scanner generates 50 "Critical" alerts, it is common for 49 of them to be complete misunderstandings of the application architecture (e.g., flagging a harmless 404 error as a data leak). On the flip side, beware of suspiciously "clean" pentest reports with zero findings—they're often a red flag for shallow testing.
This creates negative work. Your expensive engineering team ends up wasting days chasing down false positives and proving the scanner wrong instead of addressing real security concerns. It is a distraction that burns more resources than it saves. You might think you save the cost on a simple pentest but you actually pay the cost multiple times over in engineering time.
Verdict: A noisy distraction that often creates more work than value.
Level 2: Vulnerability Assessment ("Garbage In, Slightly Less Garbage Out")
This is widely sold as a "budget pentest." A human engineer takes the results of a Level 1 scan, reviews them in Excel, removes the obvious technical glitches, and hands you a report.
This suffers from a classic "Garbage In, Garbage Out" problem. Because the input relies entirely on the blind scanner from Level 1, the output is inherently limited.
- Turnaround Time: 2–5 Days.
- False Positives: Medium (Context missing).
- Quality: Low.
While the "obvious" junk is removed, the findings are still devoid of business context. The human reviewer doesn't know your app; they only know what the scanner told them. They might confirm that a specific server header is missing, but they can't tell you if that actually puts your customer data at risk.
You end up with a report full of "technically true but practically useless" findings. Your developers will still waste cycles patching low-priority issues that have zero impact on your actual business risk, while the critical logic flaws remain completely untouched.
Verdict: A polished version of a useless scan. It looks better on paper, but provides minimal security value.
Level 3: Standard Manual Pentest (The "Compliance Standard")
This is the industry standard for SOC2, ISO 27001, and critical vendor assessments. A skilled human ethical hacker actively attempts to exploit your system within a fixed timeframe (Time-Boxed), usually with partial access (Gray Box). Learn more about what artifacts you should expect from a high-quality pentest.
- Turnaround Time: 2 - 4 Weeks.
- False Positives: Some.
- Quality: Medium to High.
This is where Business Logic flaws are found. 27% of all API attacks are business logic abuses that scanners missed completely. A Level 3 penetration test acts like a malicious user, trying to bypass payment gates, escalate privileges, or manipulate IDs. These types of vulnerabilities align with the OWASP Top 10 2025, particularly around broken access control and security misconfiguration.
The quality is capped by time. If the engagement is scoped for 40 hours, the tester stops after 40 hours, regardless of what parts of the application remain untested. You are paying for effort, not necessarily total coverage. Time constraints force individuals to pick and choose only a few high-likelihood attack hypotheses and pursue them in-depth. Also because the testing is manual, a pentester can only look at one hypothesis at a time. 56% of companies receive mixed results and switch security vendors for the next pentest.
Level 4: Deep-Dive / Source-Assisted Pentest (The "Full Assurance")
This is the premium tier, often reserved for high-risk assets (fintech, healthcare, critical infrastructure). Testers are given source code access, design documents, and direct developer communication (White Box).
- Turnaround Time: 3–6 Weeks.
- False Positives: Very Few.
- Quality: High.
Testers don't just guess inputs; they read the code to find "Root Cause" vulnerabilities. They can identify deep cryptographic flaws, complex race conditions, and bad coding patterns that a black-box tester would never see.
This used to be considered the highest level of security assurance available, but also historically this was the most expensive and slowest to procure. Often leading to the software that’s being tested being out of date. By the time testing has completed, the software has typically changed dramatically. Most software can’t stop and wait six weeks before shipping a new feature.
Level 5: Supervised Agentic Penetration Testing
For decades, companies had to choose between Speed (Level 1), Cost (Level 2), and Quality (Level 3/4). You couldn't have all three. Supervised Agentic Penetration Testing, such as Casco Supervised, changes the math.
Level 5 penetration tests use agentic AI that thinks like a Level 3 human pentester, leverages the source code and other context of a Level 4 pentest, but operates at a fraction of the time. Unlike a Level 2 assessment which simply validates what a scanner already found, agentic pentesters actively hunt for new, complex attack paths.
Human experts, such as Casco’s security team staffed by ex-AWS, ex-NSA security engineers, steer the agent, review findings for false-positives and inject the critical creative strategy necessary to find subtle logic flaws and multi-step attack chains.
- Turnaround Time: A few hours to a few days.
- False Positives: Very Few.
- Quality: Maximum.
Ultimately the supervised agentic penetration test model works best and is becoming the de facto future standard for penetration testing because:
- It understands context: It can navigate complex business logic that baffles standard scanners.
- It exploits safely: It doesn't just list vulnerabilities; it proves them.
- It scales infinitely: It provides the coverage of a Level 4 deep-dive without the multi-week wait time.
Casco’s supervised penetration tests have helped companies pass FAANG penetration test reviews within a few business days. Whether you choose our fully autonomous solution or our human-supervised penetration testing, Casco ensures you never compromise on software security.
Ready to see what a real pentest looks like?
Schedule your demo with Casco today. Get your first finding for free and see how Casco finds vulnerabilities that your previous pen tests missed.