OWASP Top 10 2025: Navigating the New Security Landscape
The release of the OWASP Top 10 2025 marks a pivotal moment for application security. While some classic vulnerabilities remain, the list reflects a world where software is increasingly complex and interconnected. For security teams, this means the goalposts have moved from finding simple bugs to securing entire ecosystems.
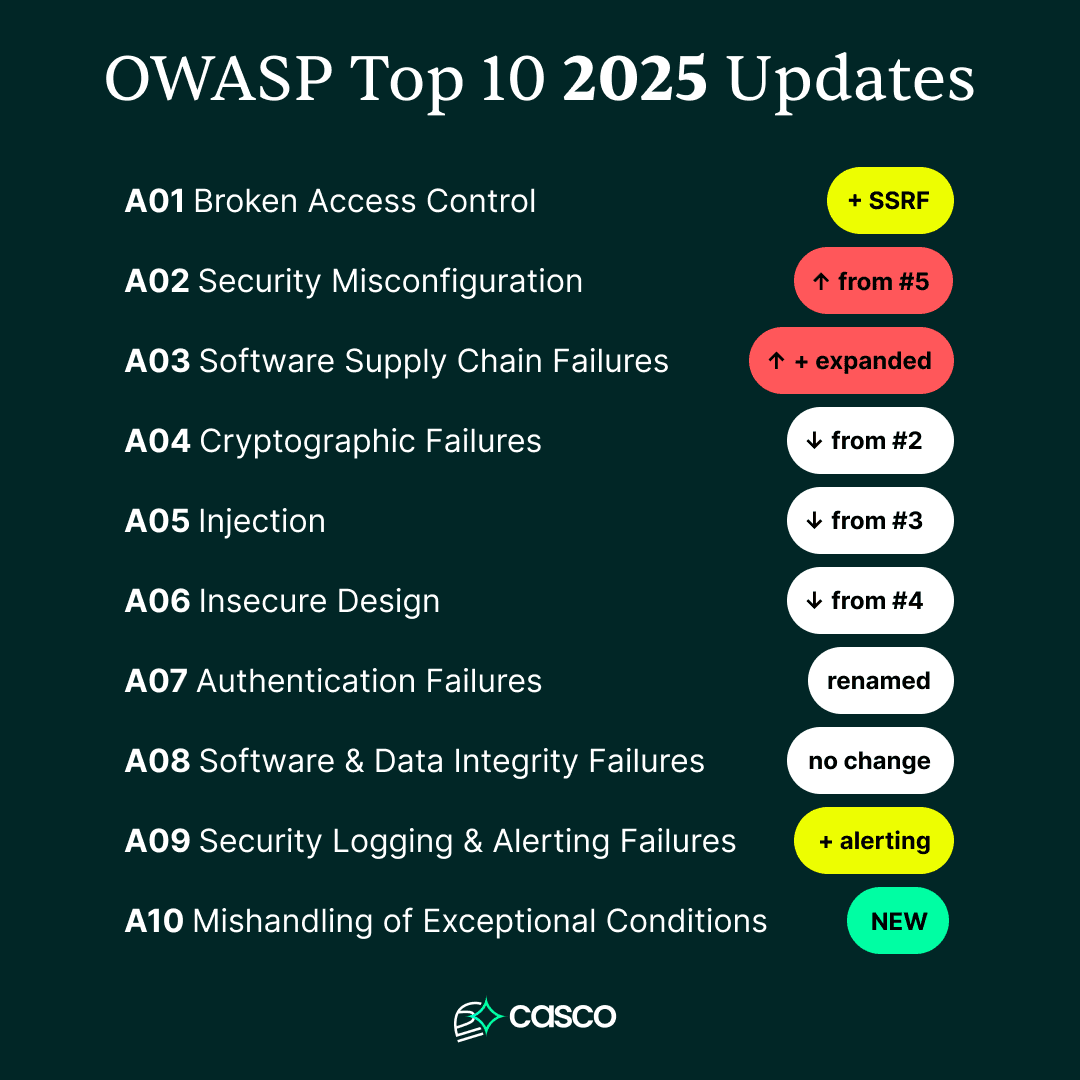
What Stayed at the Top
Broken Access Control remains the number one risk on the list. This category covers flaws that allow attackers to bypass authorization or act as other users. It is consistently the most common vulnerability found during testing.
Interestingly, Server-Side Request Forgery (SSRF) has now been folded into this category. This change acknowledges that SSRF is fundamentally an access control problem where a server is coerced into accessing internal resources. It highlights that managing "who can talk to what" is still the hardest part of modern security.
The Rise of Configuration Risks
Security Misconfiguration has surged from the fifth spot in 2021 to the second spot in 2025. This jump reflects the massive shift toward cloud-native environments and infrastructure-as-code. Modern apps are defined as much by their settings as by their source code. A single misaligned flag or an overly broad permission can now expose an entire database. We see this often in rapid development cycles where speed is prioritized over hardening.
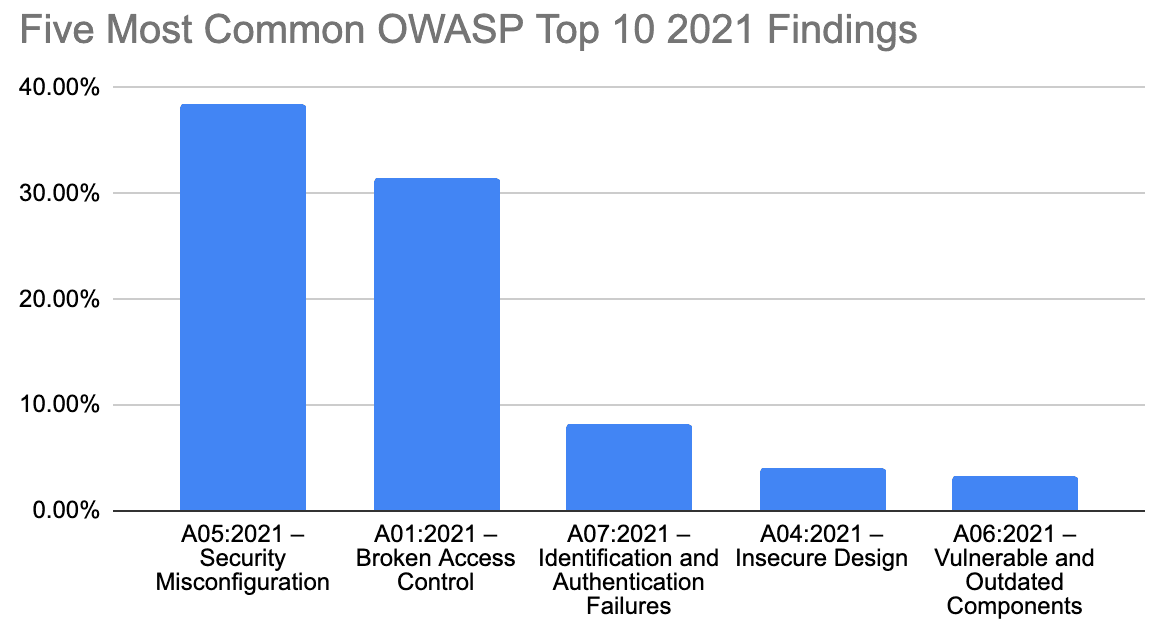
Especially in the era of vibe-coding, developers tend to trust sensible defaults. Coding agents often lack the correct context to customize those settings further. This is reflected in our own data based on the 2021 categorization. Amongst our customers, security misconfiguration makes up 38% of findings. This number is surprisingly consistent across both enterprise, mid-market, and startup customer segments. That’s even more than broken access control, which makes up 31% of all findings.
Top Movers and New Entrants: Supply Chains and Edge Cases
The most significant structural change is the debut of Software Supply Chain Failures at the third spot. This replaces the old "Vulnerable and Outdated Components" category with a much broader scope. It now covers the entire lifecycle of software, including build systems and distribution pipelines.
Mishandling of Exceptional Conditions is the other major newcomer at the tenth spot. This category focuses on how systems behave when things go wrong. Attackers often exploit poor error handling to force a "fail-open" state or leak sensitive system details. It serves as a reminder that resilience is a core component of security.
Shifts in Traditional Vulnerabilities
Injection vulnerabilities have continued their downward trend, falling to the fifth spot. Modern frameworks now handle much of the heavy lifting for input sanitization, which helps prevent classic SQL injection. However, legacy applications keep this risk relevant for many organizations.
Cryptographic Failures also dropped to the fourth spot. This does not mean encryption is less important. Rather, it suggests that better default settings in libraries are making basic encryption errors less frequent. The focus has shifted from the symptom of data exposure to the root cause of weak implementation.
How Casco Meets the 2025 Standards
Traditional scanners often struggle with the logic-heavy risks highlighted in the 2025 update. Casco’s autonomous penetration testing is designed to address these systemic weaknesses directly. Our agentic solution doesn't just look for signatures; it understands application flow, the business context, and performs exploits as authenticated users. As the OWASP list evolves, your testing strategy must evolve with it.
At Casco, we offer autonomous security testing to test against the OWASP Top 10 findings all year round. Book a demo today to get started.