Why "Clean" Pentest Reports are a Red Flag
There is a specific kind of dread that sets in when a seasoned security professional receives a pentest report with literally zero findings. Rather than feeling a sense of relief, they immediately begin to question the validity of the entire engagement. An empty report is rarely a sign of a perfect system and is almost always a sign of a shallow or poorly executed test. In the modern security landscape, a "clean" report is a red flag that suggests the testing methodology failed to uncover the inevitable risks.

The Origin of the "Perfect" Report
The concept of a clean pentest report stems from the era of Waterfall development. In that model, software was static and updates happened once or twice a year. Organizations viewed security testing as a final gate or a "check-the-box" compliance requirement before a major release. Back then, environments were stable enough that a point-in-time snapshot could reasonably represent the security posture for several months.

This legacy mindset created a culture where the goal of a pentest was to "pass" rather than to improve security. Many companies began to prioritize the appearance of safety over the reality of it. They would often restrict the testing environment or limit the testers’ access to ensure a clean outcome for auditors. If you fixed the few bugs found in a single annual window, you could claim to be secure until the following year.

The Reality of Modern Development
Today, software is never finished and the environment is never static. Most modern organizations have moved toward Agile methodologies and continuous iterations, pushing code changes daily or even hourly. A pentest report is technically outdated the moment the next pull request is merged. Expecting a single, once-a-year report to stay relevant in this high-velocity environment is no longer practical.
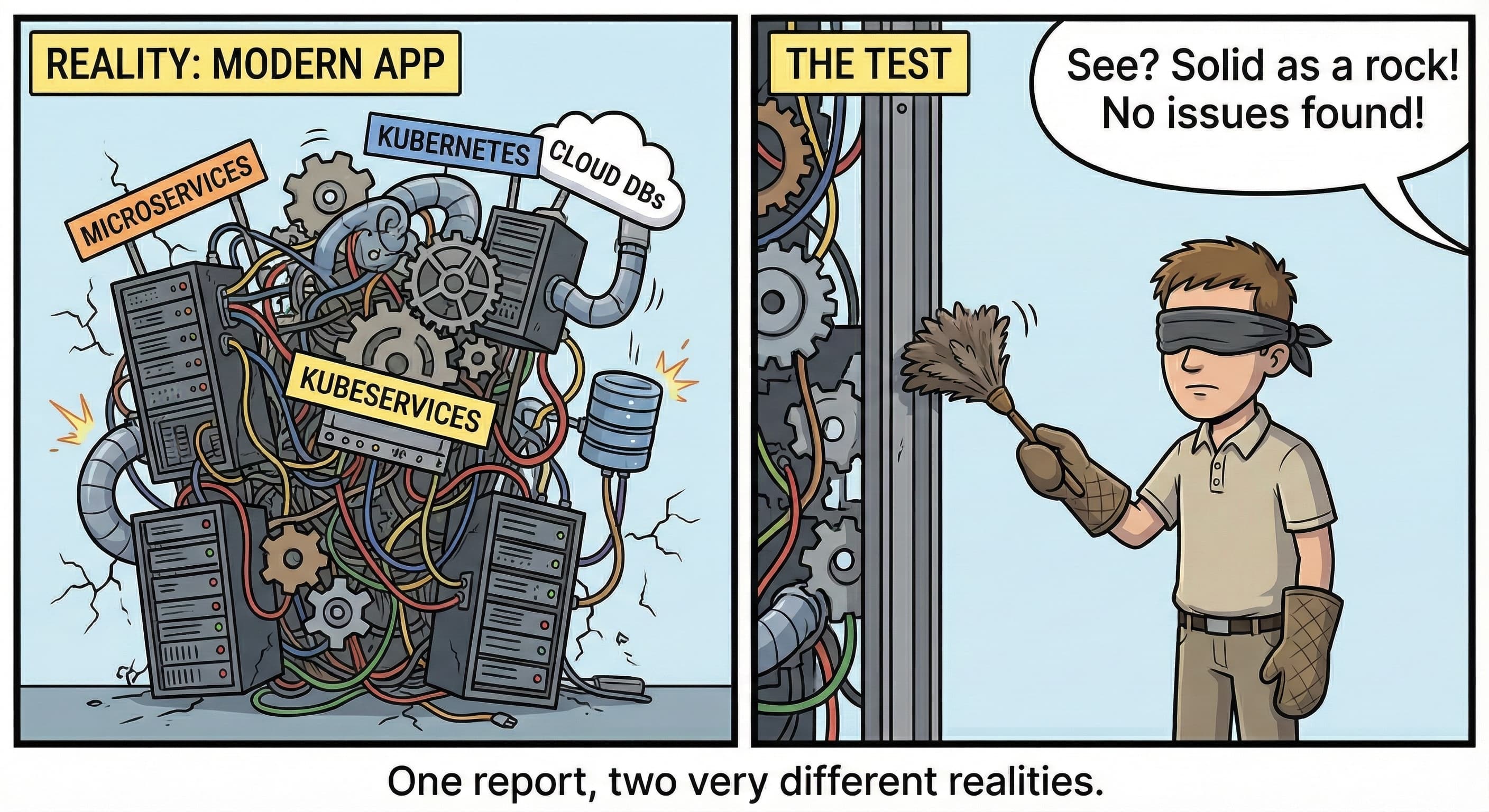
When a report comes back with zero findings, it likely means the testing methodology failed to keep pace with the complexity of the application. In a world where new vulnerabilities are discovered every hour, a total lack of findings is statistically improbable. This is why experienced security leads have stopped trusting reports that do not show at least some level of friction. They know that if the testers didn't find anything, they probably weren't looking in the right places—or they received a Level 1 or 2 assessment instead of a real penetration test.
Learning from Quality Assurance
We can see a better path forward by looking at how we handle Quality Assurance and software bugs in an Agile framework. No developer would ever claim that their enterprise software has zero bugs. Instead, the goal of a high-performing engineering team is to have a robust system for detecting and fixing those bugs. We value the speed of the feedback loop and the effectiveness of the remediation process over the initial perfection of the code.
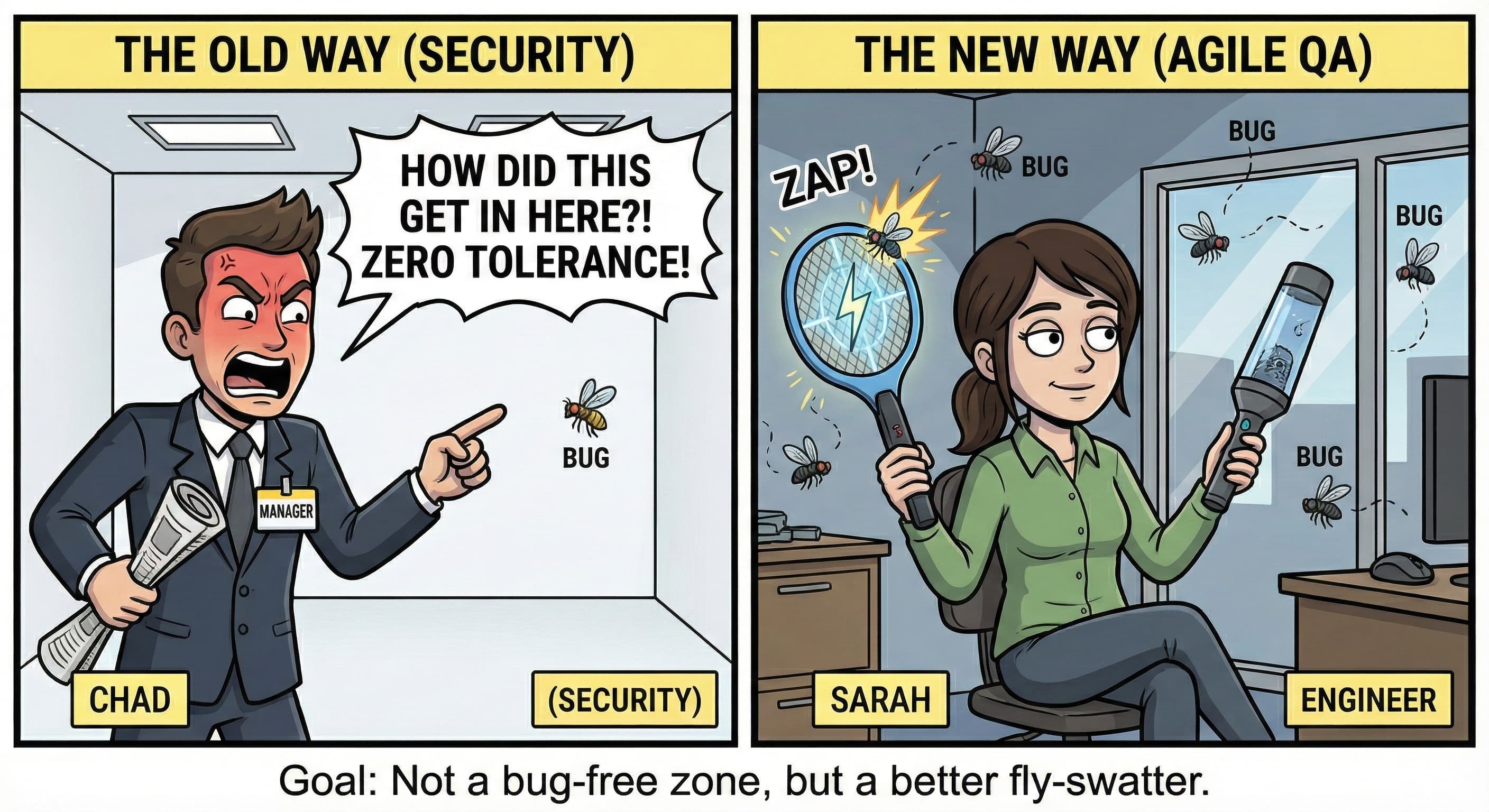
Security testing should be viewed through the same lens as continuous integration. The value of a pentest is not in the "all-clear" signal but in the quality of the vulnerabilities it uncovers. A "noisy" report full of actionable findings is infinitely more valuable than a clean one that misses the mark. It provides a roadmap for improvement and proves that the testing process is actually working as intended. Learn more about what artifacts you should expect from a high-quality penetration test.

Shifting to a Continuous Detection Cycle
The future of security lies in moving away from the artificial annual event and toward a continuous detection-and-fix cycle. This is where agentic and human-supervised testing solutions provide the most value. By running security tests much more frequently, organizations can identify risks as they are introduced. This allows for smaller, more manageable fixes rather than a massive remediation project at the end of the year.
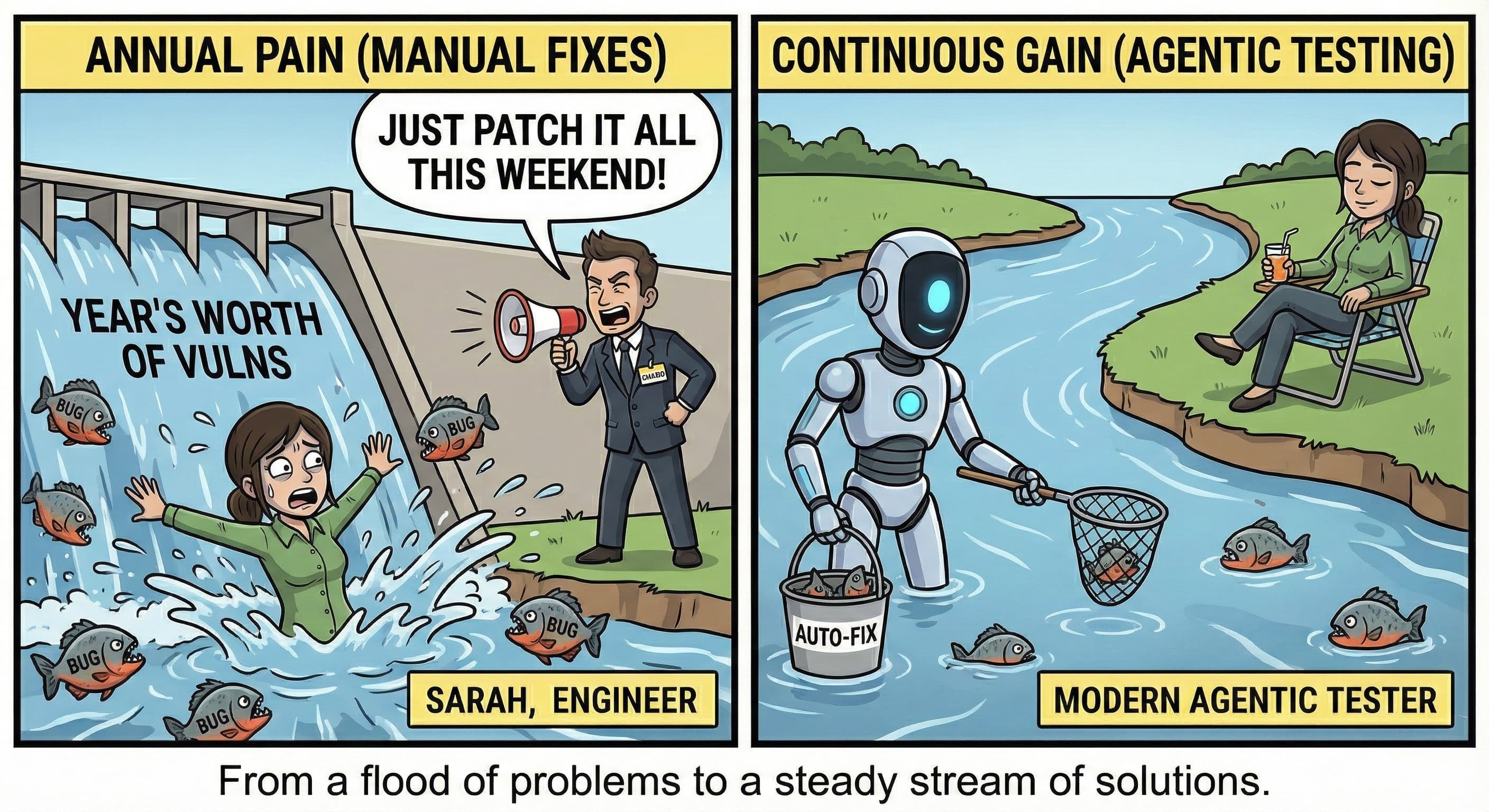
This approach creates a more honest and effective security culture. You stop aiming for a perfect score on a single day and start aiming for a resilient system that can withstand constant change. When you prioritize coverage and frequency, you build a security posture that is actually defensible. At Casco, we believe that finding a vulnerability today is always better than having an attacker find it tomorrow.

Is your security testing keeping up?
If your last pentest report was suspiciously clean, it might be time to ask if the testing was deep enough. How often does your team discover security gaps in the time between your annual audits? Reach out to us to learn how Casco's autonomous testing can provide the continuous, deep coverage your modern software environment requires.