Artifacts You Should Expect From a High-Quality Pentest
Modern security requires more than just a quick scan or a simple checkbox for compliance. When you invest in a penetration test, you are seeking a clear, unvarnished picture of your security posture and a strategic roadmap for improvement. The true value of the engagement lies in the quality of the documentation and the clarity of the remediation path provided by the testing team. Not all pentests are created equal—learn about the 5 levels of penetration testing to understand what you're actually getting.

A professional pentest should result in a series of distinct, high-fidelity artifacts. These documents easily show proof of impact and help your technical teams identify and fix vulnerabilities. Understanding what these files contain is the first step toward building a more resilient and secure infrastructure.
The Initial Penetration Test Report
The first and most critical artifact is the Initial Penetration Test Report. This document captures the state of your environment at a specific point in time and serves as a baseline for your security journey. It should be exhaustive and detail every successful exploit, misconfiguration, and discovered vulnerability within the agreed-upon scope.
A high-quality initial report must include several key components to be truly actionable.
- Executive Summary: A high-level overview of the findings tailored for stakeholders and non-technical leadership. It should translate technical risks into business impact, explaining how vulnerabilities could affect revenue, reputation, or operations.
- Methodology and Scope: A clear definition of what was tested and the specific techniques used during the engagement. This ensures that everyone understands the boundaries of the test and the rigor applied to the assessment.
- Finding Details: A detailed description of each finding, including the potential impact on the business. This section should explain not just what is broken, but why it matters in the context of your specific environment.
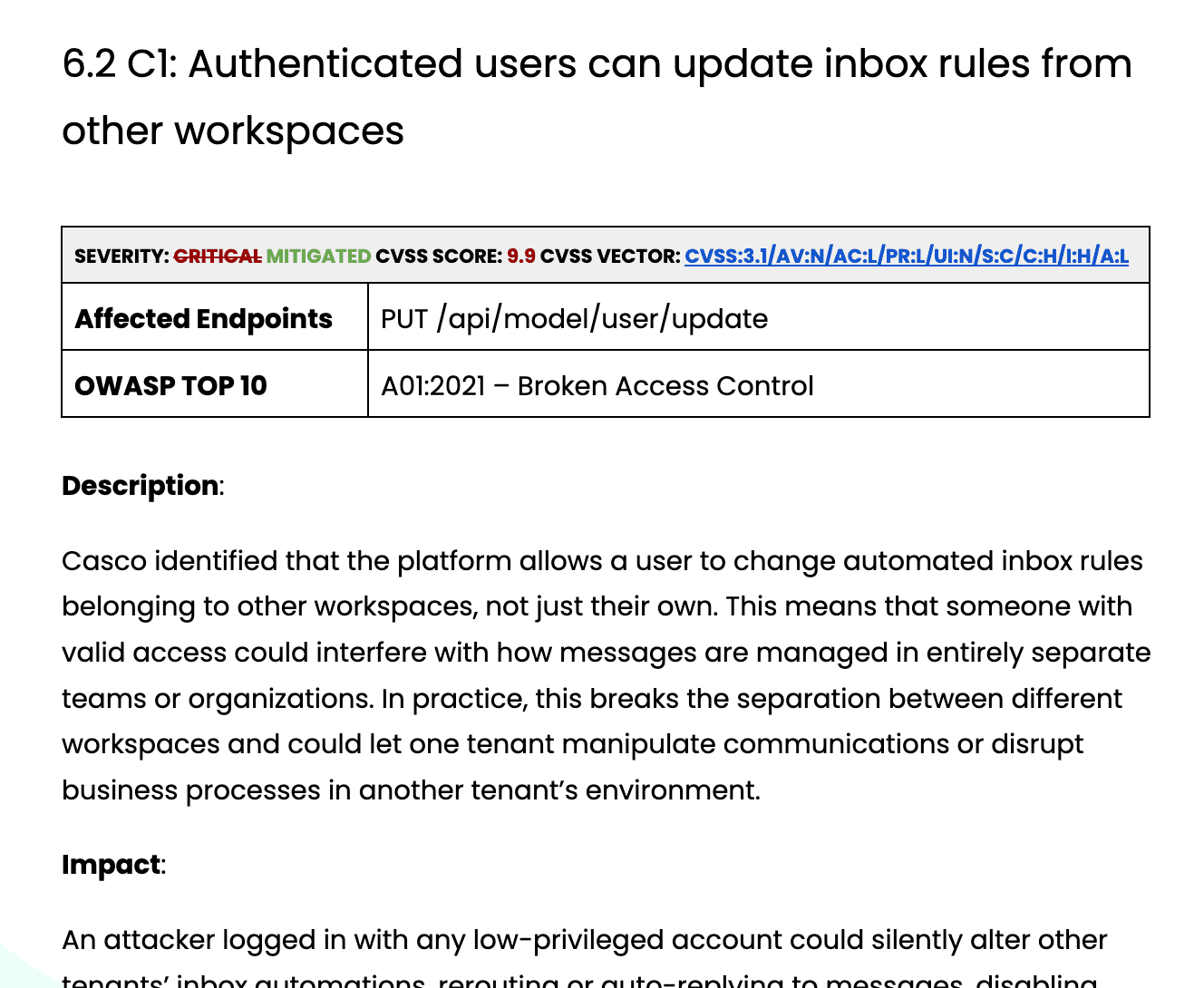
- Reproduction Steps: Precise instructions that allow your internal teams to recreate the vulnerability for verification. This removes guesswork and ensures that developers can confirm the issue before and after applying a fix.
- Prioritized Recommendations: A list of fixes ranked by risk level so your team knows what to address first. This helps in resource allocation, ensuring that "critical" and "high" risks are mitigated before moving to lower-priority items.
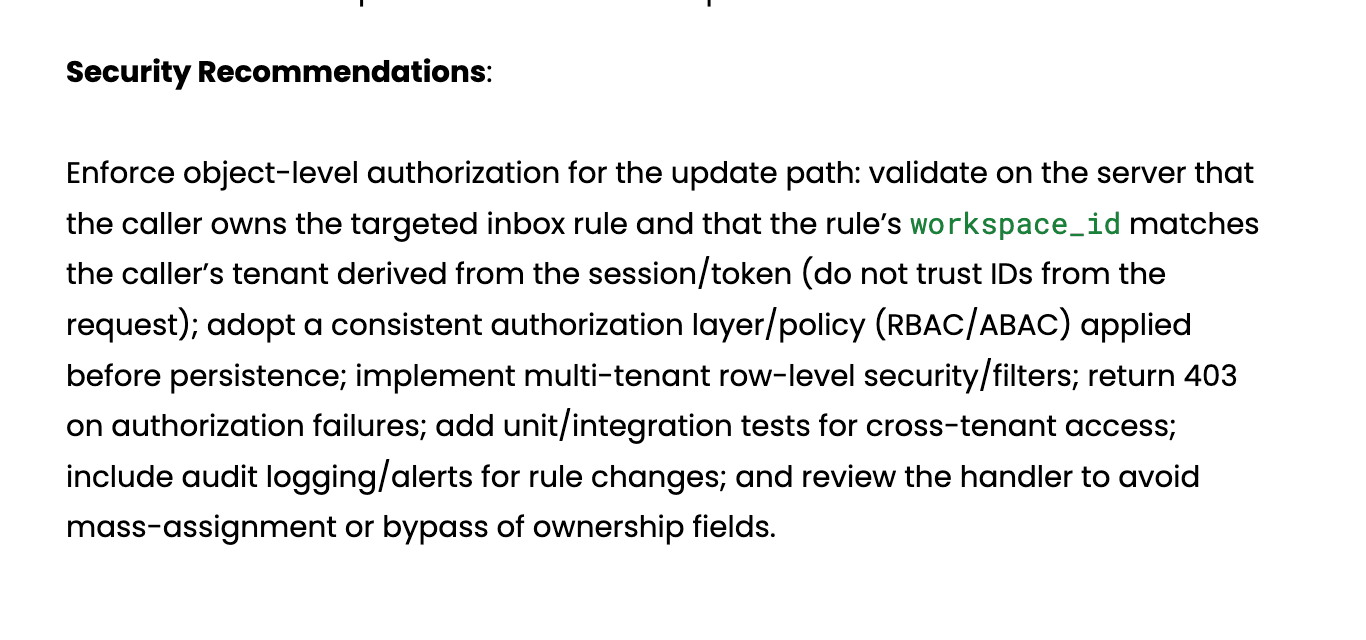
The Remediation Verification Report
Many companies make the mistake of stopping after the first report is delivered. However, true security is an iterative and ongoing process rather than a one-time event. A Remediation Verification Report is generated after your technical team has implemented the recommended fixes and the testers have returned to validate them.
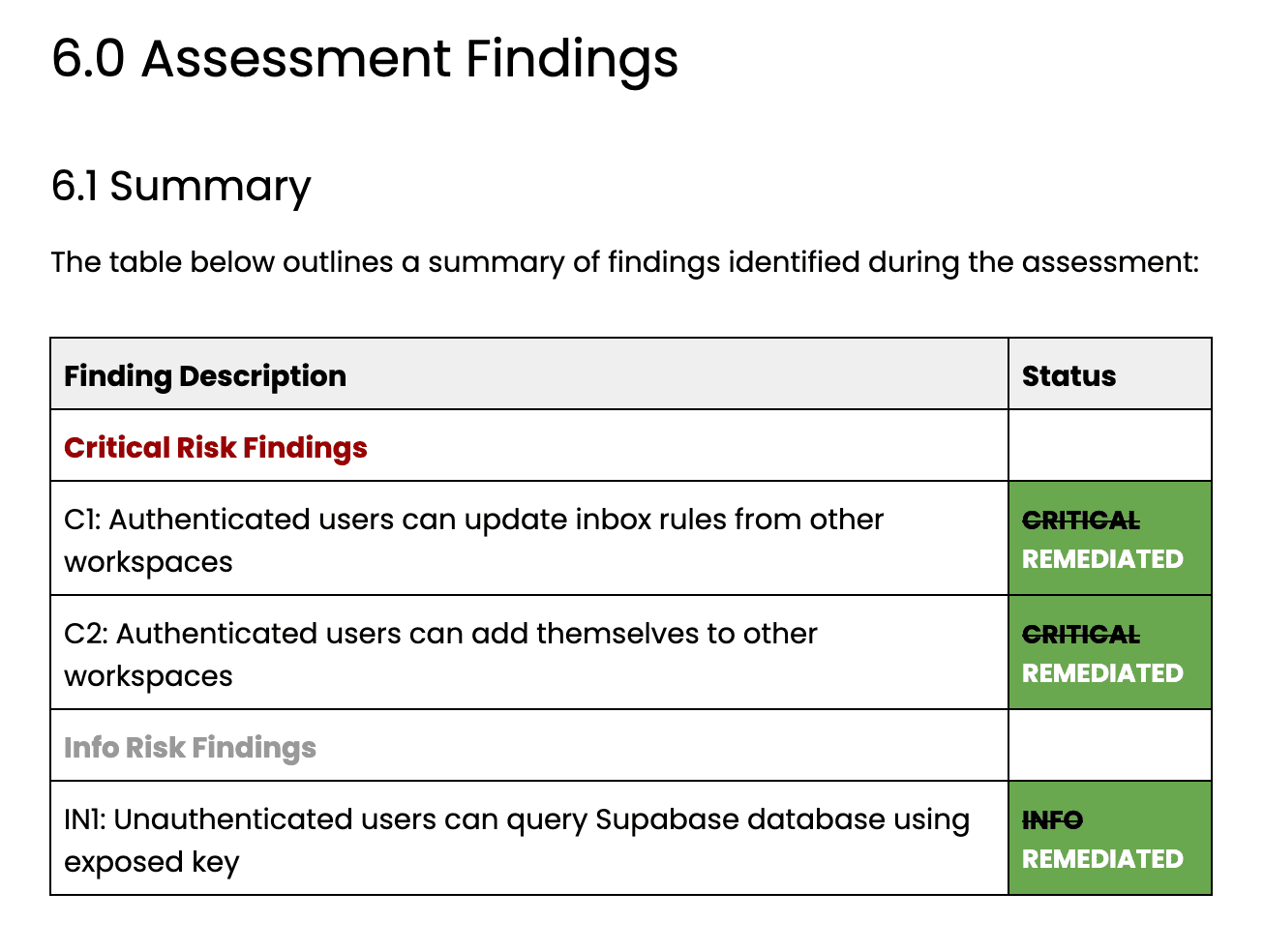
This artifact proves that the vulnerabilities identified in the first round are actually closed. It provides a historical record of your team's responsiveness to security threats and their ability to execute on technical guidance. This is often the most important document for auditors and customers because it shows active, successful management of known risks.
"Clean" Reports and Why You Should Avoid Them
You might be tempted to ask for a "clean" report that shows zero findings after remediation. We strongly discourage this practice because it is often seen as a major red flag by sophisticated partners and regulators. Large, publicly listed companies usually view a perfectly clean report with a high degree of skepticism. Read more about why "clean" pentest reports are actually a red flag.
During our time working at FAANG companies, a pentest report with zero findings was a major cause for concern during vendor assessments. It suggests that the test was either too shallow, the scope was too restricted, or that findings were intentionally omitted to look better on paper. Modern systems are incredibly complex and a report should reflect the messy reality of the testing process. A professional organization values transparency and honesty over a curated, artificial image of perfection. Showing that you found five critical bugs and fixed all five is significantly more impressive than claiming you had none to begin with.
Hence whenever, Casco's customers requests a pentest report for their FAANG or enterprises clients like OpenAI, Nvidia, or Meta, we always provide a remediation verification report as the primary artifact.
Artifact Transparency, Recency, and Compliance
The artifacts mentioned above provide the necessary paper trail for SOC2, HIPAA, or ISO certifications by demonstrating a robust "find-and-fix" cycle. However, the traditional annual penetration test is becoming obsolete as teams deploy code daily. A security snapshot from six months ago holds little relevance in a fast-moving CI/CD environment.
Waiting a full year to identify vulnerabilities creates a massive window of exposure. High-frequency or continuous penetration testing narrows this window and ensures that new features do not introduce critical flaws. This shift allows security to become an integrated part of the development lifecycle rather than a periodic roadblock.
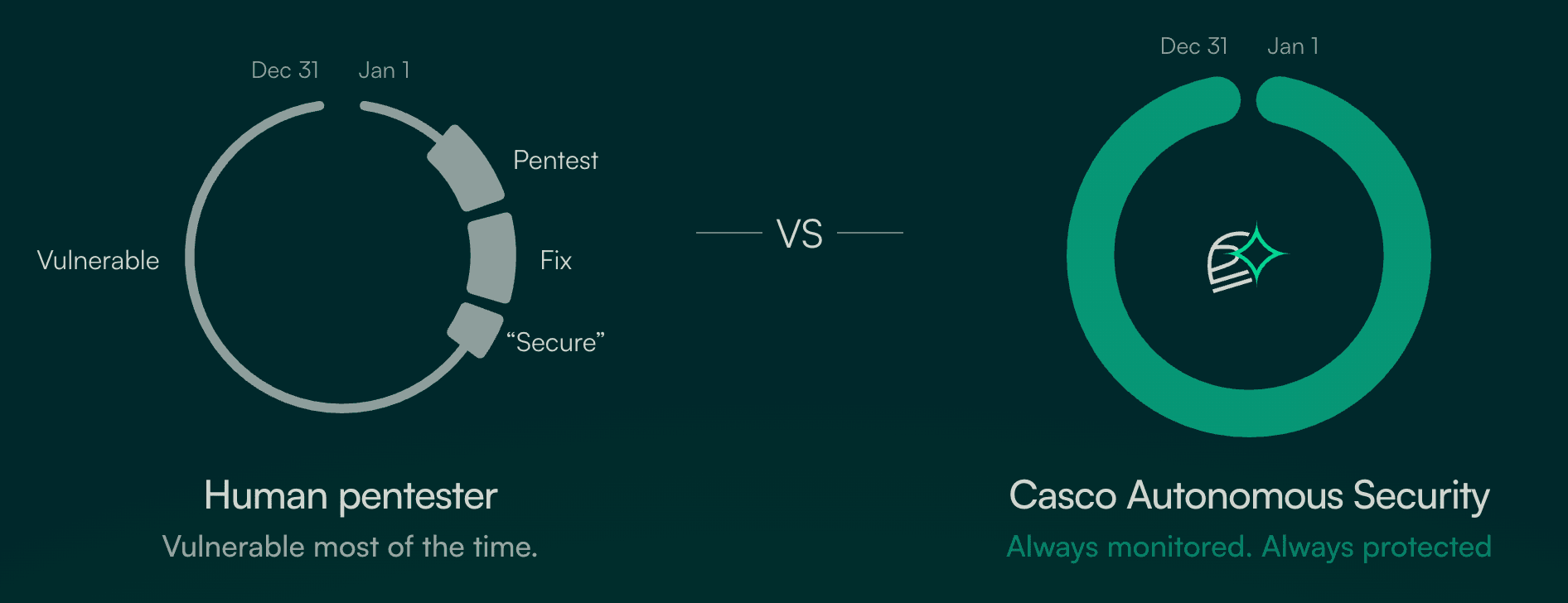
Providing a full history of your security journey is far more persuasive to enterprise clients than a single sheet of paper claiming perfect security. It proves that your organization views security as an evolving process and has the systems in place to handle emerging threats. This level of maturity is what separates industry leaders from those simply trying to pass a check.
Review Best Practices with the Casco team
Book a demo to view some of our redacted penetration test artifacts and see firsthand the level of detail we provide. During the session, you can discuss security best practices and your specific infrastructure needs with our team of former FAANG and NSA security reviewers.