Building Self-Securing Software
Traditional security testing often feels like trying to catch a moving target while standing still. Most companies rely on periodic pentests that only capture a single moment in their development cycle. This reactive approach leaves massive windows of opportunity for attackers to exploit new vulnerabilities. At Casco, we believe that all software should be effortlessly secure.
The current landscape of cybersecurity is shifting toward a model of continuous intelligence. Human-only penetration testing is inherently limited by time and scale. Even the most talented security researchers cannot monitor every line of code across an entire enterprise twenty-four hours a day. We are moving toward a future where security is not an event but a constant state of being.
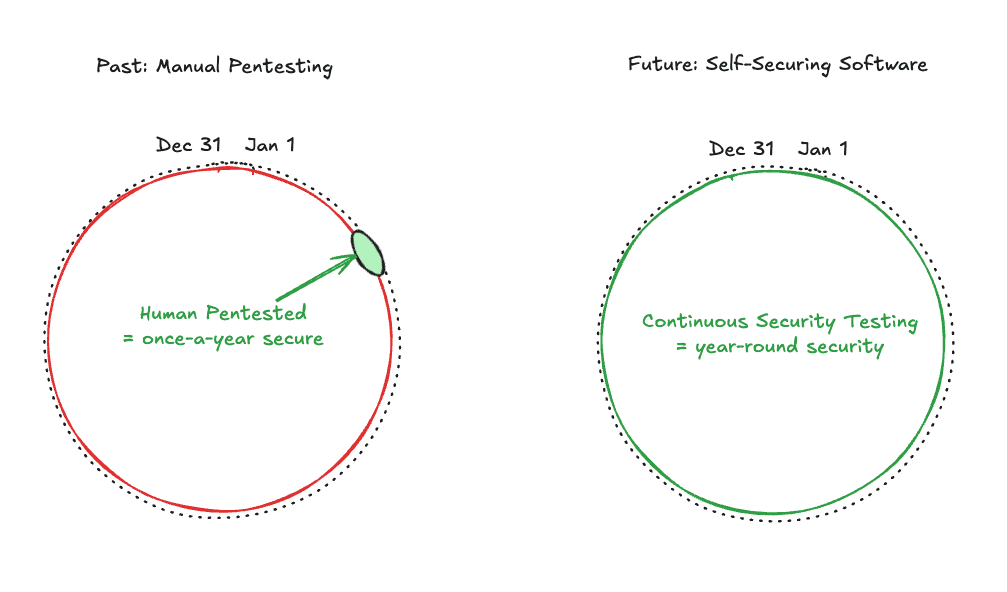
The Rise of the 24/7 Security Engineer
Agents represent the next major leap in offensive security. Unlike traditional automated scanners, agentic systems possess the ability to reason and adapt to complex environments. These agents can operate independently to explore attack surfaces and identify deep-seated logic flaws. They do not require sleep or breaks. This allows for a level of coverage that was previously impossible for even the largest security teams to achieve.
When security testing runs autonomously and continuously, the window for exploitation shrinks significantly. Security testing against running applications can yield findings that are simply impossible to detect via static code analysis. This coverage and speed ensures that the offensive side of security keeps pace with the rapid speed of modern software development. It transforms the security team from a bottleneck into an enabler of fast and safe innovation.
Imagine a subdomain takeover. This attack occurs when an attacker gains control over a legitimate subdomain (e.g., blog.example.com) because it points to an external service or IP address that has been decommissioned but not updated in the DNS records. This commonly happens when a "dangling" CNAME record remains active after a cloud resource is deleted. An attacker can claim that same identifier on the provider’s platform and host malicious content under the victim's domain. There’s no static code analysis tool that could catch this issue. But a security testing agent that runs 24/7 can verify immediately that you have a dangling subdomain.
Closing the Loop with Coding Agents
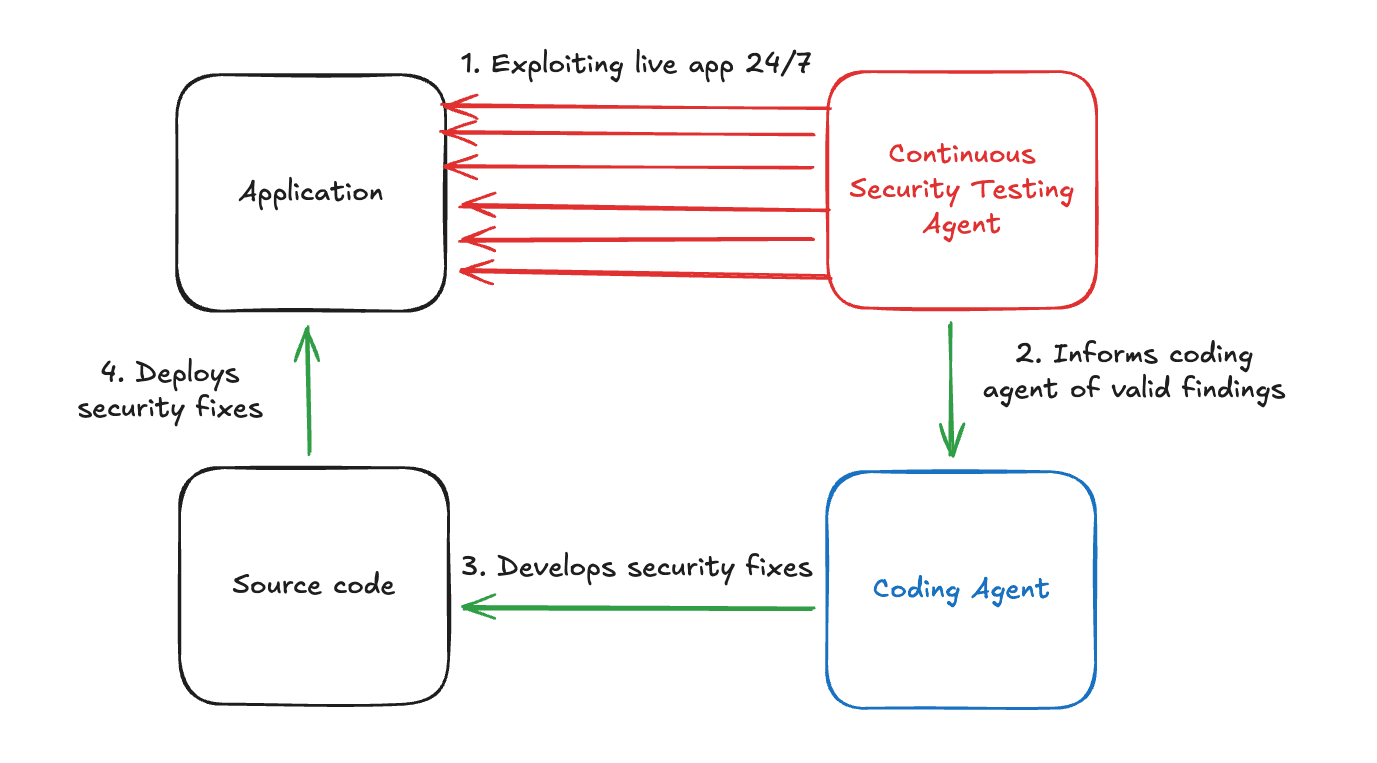
The true power of autonomous testing is realized when it connects directly to remediation. We envision a world where an offensive AI agent identifies a flaw and immediately communicates with a coding agent like Continue. This coding agent can then generate, test, and propose a patch for the specific vulnerability. This creates a closed loop that eliminates the lag time between discovery and fix.
This integrated approach removes the friction of manual ticketing systems and back-and-forth communication between departments. A vulnerability found at 2:00 AM can be addressed and neutralized before the start of the next business day. Humans can remain in the loop to supervise and provide high-level guidance. However, the heavy lifting of remediation is handled effortlessly by the agents themselves.
Making Software Effortlessly Secure
Our mission at Casco is to make all software effortlessly secure. We want to remove the burden of constant worry from developers and security professionals alike. By leveraging agents, we can provide a level of protection that outperforms human-only solutions. The goal is to reach a state where software fixes itself as quickly as new threats appear.
This vision of "Continuous AI" is not just a theoretical concept. As these agents become more sophisticated, the cost of maintaining high-quality security will drop while the effectiveness rises. We are proud to be at the forefront of this transformation.
Get year-round security with autonomous security testing. Get started at https://casco.com